1- Windows - Start - Run - charmap
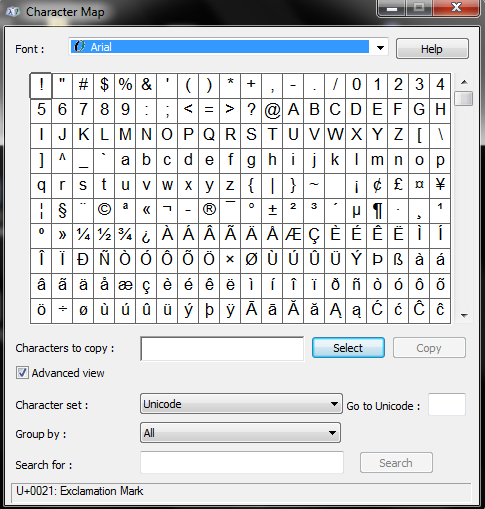
2- Find U+202E (RTLO) in charmap . We can use the "Go to Unicode" function for this in the charmap program. We just need to type in 202E in the box and the program will find the character for you.
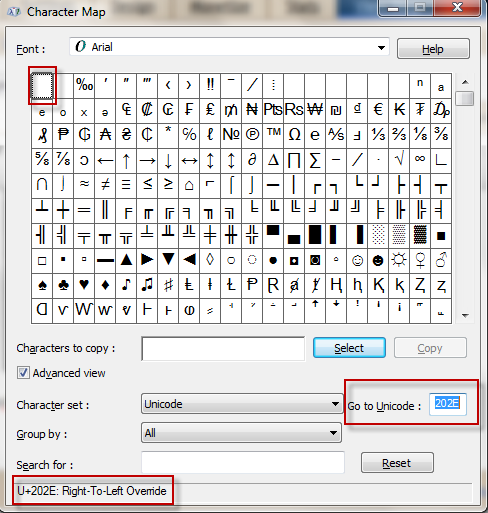
3- Now that we found the character, we gotta copy it.Use the select & copy functions.
4- Now, we'll use our favorite "notepad.exe" to test the RTLO spoofing.
Note: We're using "notepad.exe" just for demonstration, in real scenario the attacker would use the same technique for the "malware binary".
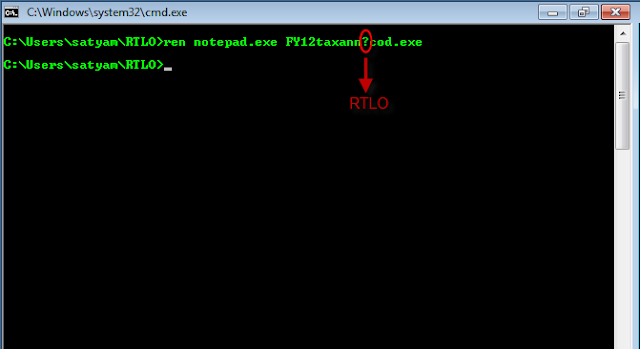
Let's save a copy of notepad.exe to a test directory and open windows command prompt "cmd".Then rename the file to something "interesting & intelligent ".
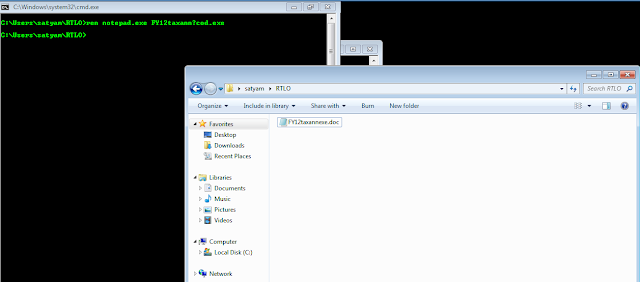
So, we've successfully renamed "notepad.exe" to "FY12taxannexe.doc", with the below command
ren notepad.exe FY12taxann?cod.exe
for a novice user it's a "DOC" file but windows runs it as an executable. We can modify the extension to anything of choice (jpg,png etc.)
Now lets's understand how it worked ?
ren notepad.exe FY12taxanncod.exe
örnekler
[RTLO]cod.stnemucodtnatropmi.exe [RTLO]cod.yrammusevituc[LTRO]n1c[LTRO].exe [RTLO]gpj.!nuf_stohsnee[LTRO]n1c[LTRO].scr
alternatif yöntem
http://www.wildhacker.com/2012/06/extension-changing-tutorial-how-to-run.html


